OAuth 2.0 SSO 概述
OAuth 2.0 是一个授权框架,可使应用程序通过 HTTP 服务获得对用户帐户的有限访问权限。它的工作原理是将用户身份验证委托给托管用户帐户的服务,并授权第三方应用程序访问用户帐户。OAuth 2.0 为 web、桌面应用程序以及移动设备提供授权流。
基本 SSO
无论你选择了哪种功能,基本 SSO 都需要一些特定的数据,特别是公钥。添加会员积分或信用卡集成功能将需要额外的信息。
设置信息
要正确设置模板网站的 OAuth 2.0 SSO 访问权限,我们需要以下内容:
- API(授权、令牌、userProfile)
- ClientId
- 客户端密钥
- ResponseMode
- isNonceEnabled
- customerDetailsAPIKey(如有)
授权流程
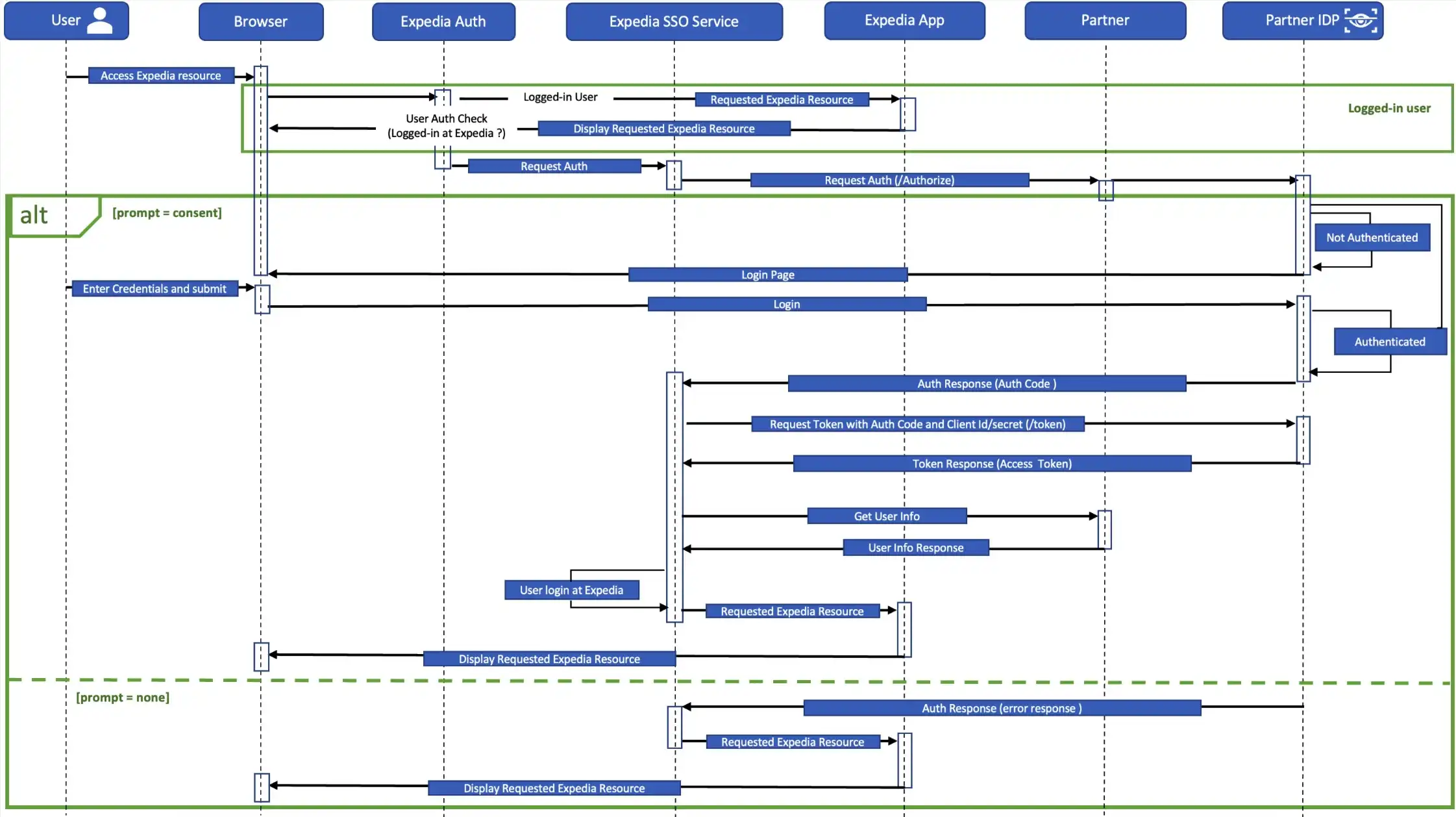
授权端点
GET /authorize 端点用于身份验证和授权。当用户是 logged-in 时,它会向客户端返回授权许可或代码。这是一个浏览器重定向。
| 字段 | 说明 | 数据类型 | 示例值 | 是否必填? |
|---|---|---|---|---|
client_id | 用于识别客户端。必须与身份供应商 (IDP) 中预先注册的值一致。通过手动客户端注册或动态客户端注册 API 获取。 | 字符串 | 是 | |
nonce | 用于减轻重放攻击。该值将在 ID 令牌中返回。 | 字符串 | 是 | |
prompt | 验证所需的交互类型。如果为“空”,则用户必须登录(如果尚未经过身份验证)。如果为“无”,则 IDP 将不会提示登录,但如果已登录则会返回授权码,否则会返回错误。 | 字符串 | 有效值: none 或 为空 | 否 |
redirect_uri | 发送授权码或令牌的回调位置。必须与客户端注册时在 IDP 中预先注册的值一致。 | 字符串 | 是 | |
response_type | code (IDP) 值。 | 字符串 | 是 | |
response_mode | 返回授权响应的方式。 | 字符串 | 有效值: query | 否 |
scope | 访问令牌,用于获取个人资料详细信息。身份验证请求必填。 | 字符串 | 个人资料和电子邮件 | 是 |
state | 互动状态。该值会在令牌中返回,使用户能够点击进入、验证并返回到他们最初感兴趣的页面。该值可包含字母数字、逗号、句点、下划线和连字符。 | 字符串 | 是 | |
ui_locales | 用户首选的用户界面语言和脚本。 | 字符串 | en_CA, fr_CA | 否 |
audience | 预期的收件人。 | 字符串 | 由合作伙伴定义 | 否 |
响应参数
| 参数 | 说明 | 数据类型 | 是否必填? |
|---|---|---|---|
code | 用于识别客户端的授权码。它必须与 IDP 中预先注册的值一致。通过手动客户端注册或动态客户端注册 API 获取。 | 字符串 | 是 |
state | 互动状态。该值会在令牌中返回,使用户能够点击进入、验证并返回到他们最初感兴趣的页面。该值可包含字母数字、逗号、句点、下划线和连字符。 | 字符串 | 是 |
授权 URL 示例
https://example.com/authorize?client_id={clientID}&response_type=code&state=d6b93799-404b-4205-9bb3-c579b1180428&scope=email profile&nounce=234567687867&redirect_uri=https://{ExpediaDomain}/sso/auth回调 URL 示例
https://{ExpediaDomain}/sso/auth?code=12345678&state=d6b93799-404b-4205-9bb3-c579b1180428令牌端点
POST /token端点是一个后端 API 调用,用于通过提供授权许可或代码来获取访问令牌和 ID 令牌。
请求参数
| 参数 | 说明 | 数据类型 | 是否必填? |
|---|---|---|---|
grant_type | IDP 用来授权令牌生成的机制。值:authorization_code | 字符串 | 是 |
redirect_uri | 指定发送授权的回调位置。该值必须与用于生成原始 authorization_code 的 redirect_uri 一致。 | 字符串 | 是 |
code | /authorize 调用响应中收到的客户端识别码。 | 字符串 | 是 |
请求标头
| 参数 | 说明 | 数据类型 | 示例值 | 是否必填? |
|---|---|---|---|---|
accept | 必须为“application/json” | 字符串 | application/json | 是 |
authorization | 用 Base64 编码客户端 ID 和秘钥。使用 HTTP 授权标头中的编码信息。 | 字符串 | Basic<Base64 encoded client ID and secret> | 是 |
Content-Type | 必须为“application/x-www-form-urlencoded” | 字符串 | application/x-www-form-urlencoded | 是 |
响应属性
| 字段 | 说明 | 数据类型 |
|---|---|---|
access_token | 访问令牌 | 字符串 |
token_type | 令牌的受众 | 字符串 |
expires_in | 访问令牌的过期时间(以秒为单位) | 整数 |
scope | 访问令牌中包含的作用域 | 字符串 |
示例令牌 CURL
curl --location 'https://example.com/token’ \
--header 'Content-Type: application/x-www-form-urlencoded' \
--header 'Authorization: Basic {encoded ClientID:clientSecret}' \
--data-urlencode 'grant_type=authorization_code' \
--data-urlencode 'redirect_uri=https://{ExpediaDomain}/sso/auth’ \
--data-urlencode 'code={Authorization code after login as part of callback to Expedia /sso/auth endpoint}'令牌响应示例
{
"access_token": "eyJhbGciOi.JSUzI1NiIsImtpZCI6Ilk1MkFDVXd3QV9SUzI1NiIsInBp.LmF0bSI6ImlrY20ifQ",
"token_type": "Bearer",
"expires_in": 1799
}用户信息端点
GET /userinfo 端点是一个后端 API 调用,它根据提供的访问令牌返回有关经过身份验证的用户的声明。
请求标头
| 字段 | 说明 | 数据类型 | 示例值 | 是否必填? |
|---|---|---|---|---|
ClientId | 用于识别客户端。必须与身份供应商 (IDP) 中预先注册的值一致。通过手动客户端注册或动态客户端注册 API 获取。 | 字符串 | 是 | |
Authorization | 用于发送凭证或令牌来验证用户的 HTTP 标头 | 字符串 | 持有者 [access_token] | 是 |
响应
| 字段 | 说明 | 数据类型 | 示例值 | 是否必填? |
|---|---|---|---|---|
membershipId | 唯一标识客户账户的标识符 | 字符串 | 是 | |
optIn | 如果客户选择接收营销电子邮件,则为布尔标记 | 布尔值 | 正确/错误 | 否 |
languageId | 用户的首选语言 | 字符串 | 英语、法语 | 否 |
channelType | 用户与应用程序交互的不同平台 | 字符串 | 网络、手机、平板电脑 | 否 |
firstName | 客户的名字 | 字符串 | 是 | |
middleName | 客户的中间名 | 字符串 | 否 | |
lastName | 客户的姓氏 | 字符串 | 否 | |
email | 客户的电子邮件地址 | 字符串 | 否 | |
programAccount | Loyalty-related 信息 | programAccount | 有关对象详细信息,请参阅下面的 Add loyalty -> programAccount 部分 | 否 |
示例用户信息 CURL
curl --location 'https://example.com/userinfo' \
--header 'client_id: {clientId}' \
--header 'Authorization: Bearer {acess_token from token endpoint}'示例 Userinfo 响应
{
"membershipId": "12345678",
"languageID": "en",
"middleName": "MiddleName",
"lastName": "LastName",
"firstName": "FirstName",
"email": "test@expediagroup.com",
"programAccount": {
"programId": "Gold",
"loyaltyAccountBalance": {
"value": "10000",
"currency": "Points"
}
}
}添加会员积分
作为模板网站功能的一部分,您可以让客户通过旅行消费获得会员积分。如果您愿意,您的模板还可以支持客户[使用他们累积的会员积分]loyalty()兑换旅游产品。
设置要求与标准实施的设置相同,许多值也是如此。这里只包括那些有所不同的值。
除了标准user information之外,忠诚度计划设置还将包括以下值。
programAccount
| 字段 | 说明 | 数据类型 | 是否必填? |
|---|---|---|---|
programId | 客户所属会员计划的标识符或与会员计划相关的等级名称 | 字符串 | 是 |
loyaltyAccountNumber | 客户会员帐号;只有在会员操作需要辅助标识符(除唯一的 membershipId 外)时才应填入 | 字符串 | 否 |
lastFourDigitsOfCreditCard | 客户预订所用信用卡的最后 4 位数 | 整数 | 否 |
accountName | 计划名称(如果与等级名称不同) | 字符串 | 否 |
loyaltyConversionRatio | 消费金额转换为累积积分的比率(例如 $1 = 1 积分) | 双倍 | 否 |
loyaltyAccountBalance | 客户累积会员积分的当前余额 | 金额 (有关对象详细信息,请参阅下面的金额部分) | 否 |
金额
| 字段 | 说明 | 数据类型 | 是否必填? |
|---|---|---|---|
value | 会员积分余额;嵌套在 loyaltyAccountBalance 之下 | 隆 | 是 |
currency | 会员计划使用的奖励货币,例如货币类型、积分和里程;嵌套在 loyaltyAccountBalance 之下 | 字符串 | 是 |