OAuth 2.0 SSO overview
OAuth 2.0 is an authorization framework that enables applications to obtain limited access to user accounts on an HTTP service. It works by delegating user authentication to the service that hosts the user account, and authorizing third-party applications to access the user account. OAuth 2.0 provides authorization flows for web and desktop applications, and mobile devices.
Basic SSO
Regardless of the feature choices you’ve selected, basic SSO requires some specific data, particularly a public key. Adding loyalty or credit card implementations will require additional information.
Setup information
To properly set up the OAuth 2.0 SSO access to your template site, we need a few things, including:
- APIs (authorize, token, userProfile)
- ClientId
- Client secret
- ResponseMode
- isNounceEnabled
- customerDetailsAPIKey (if available)
Authorization Flows
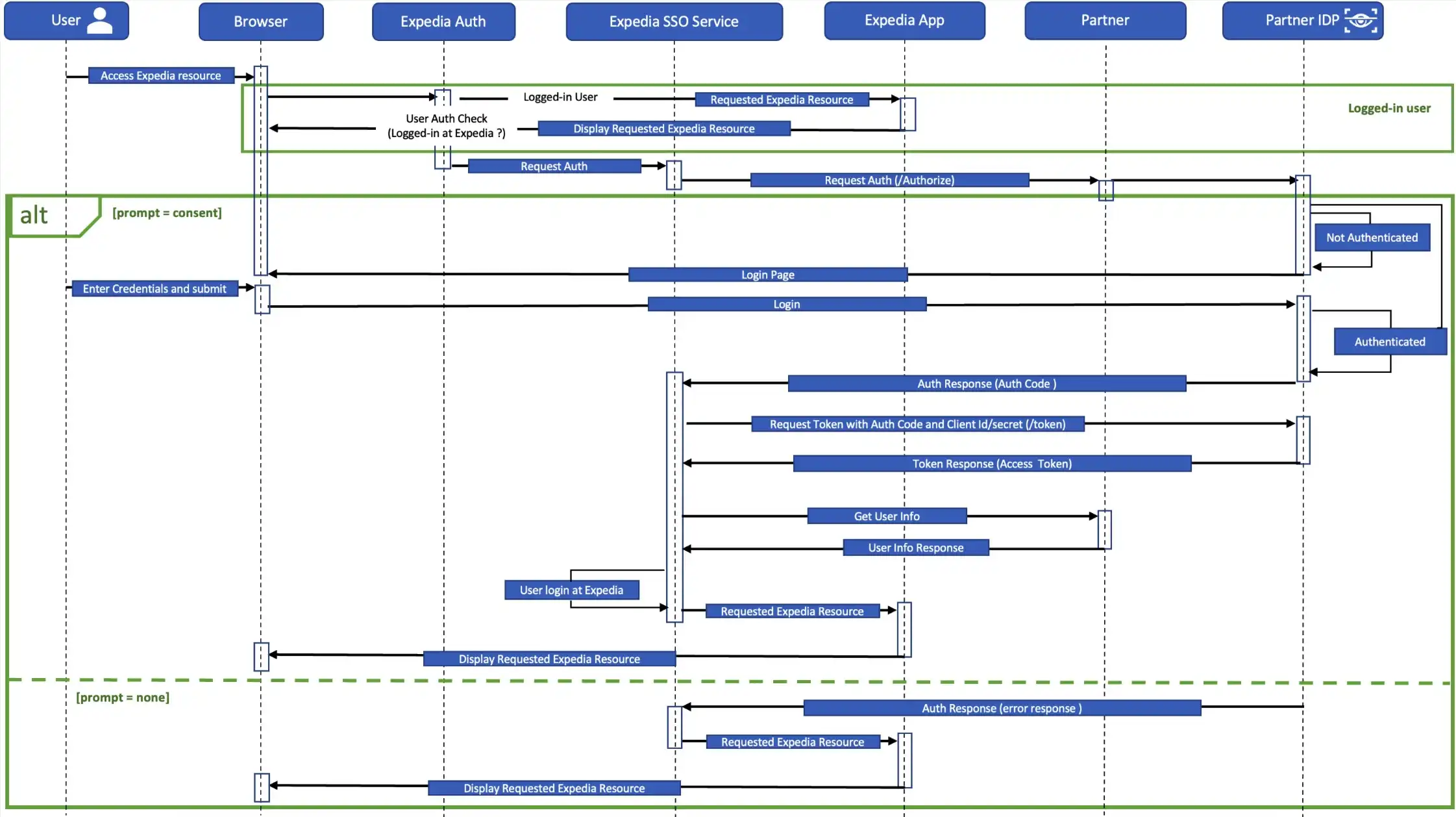
Authorize endpoint
The GET /authorize endpoint is used for authentication and authorization. It returns an authorization grant or code to the client post user is logged-in. It is a browser redirect.
| Field | Description | Data type | Sample value | Mandatory? |
|---|---|---|---|---|
client_id | Identifies the client. Must match the value preregistered in your identity provider (IDP). Obtained during either manual client registration or via the Dynamic Client Registration API. | String | Yes | |
nonce | Used to mitigate replay attacks. This value is returned in the ID token. | String | Yes | |
prompt | The type of interaction required to validate. If "empty", the user must log in if not already authenticated. If "none," the IDP won't prompt for login but will return an authorization code if logged in, or an error otherwise. | String | Valid values: none OR EMPTY | No |
redirect_uri | Callback location where the authorization code or tokens should be sent. Must match the value preregistered in your IDP during client registration. | String | Yes | |
response_type | code (IDP) value. | String | Yes | |
response_mode | How the authorization response should be returned. | String | Valid value: query | No |
scope | Access token, used for fetching profile details. Required for authentication requests. | String | profile and email | Yes |
state | The state of the interaction. This value is returned in the token, and enables the user to click through, authenticate, and be returned to the page they’re originally interested in. The value can contain alphanumeric, comma, period, underscore, and hyphen characters. | String | Yes | |
ui_locales | User's preferred languages and scripts for the user interface. | String | en_CA, fr_CA | No |
audience | The intended recipient. | String | Defined by Partners | No |
Response parameters
| Parameter | Description | Data type | Mandatory? |
|---|---|---|---|
code | Authorization code that identifies the client. This must match the value preregistered in your IDP. Obtained during either manual client registration or via the Dynamic Client Registration API. | String | Yes |
state | The state of the interaction. This value is returned in the token, and enables the user to click through, authenticate, and be returned to the page they’re originally interested in. The value can contain alphanumeric, comma, period, underscore, and hyphen characters. | String | Yes |
Sample Authorize URL
https://example.com/authorize?client_id={clientID}&response_type=code&state=d6b93799-404b-4205-9bb3-c579b1180428&scope=email profile&nounce=234567687867&redirect_uri=https://{ExpediaDomain}/sso/authSample Callback URL
https://{ExpediaDomain}/sso/auth?code=12345678&state=d6b93799-404b-4205-9bb3-c579b1180428Token endpoint
The POST /token endpoint is a backend API call which is used to obtain an access token and ID token by presenting an authorization grant or code.
Request parameters
| Parameter | Description | Data type | Mandatory? |
|---|---|---|---|
grant_type | The mechanism your IDP uses to authorize the creation of the tokens. Value: authorization_code | String | Yes |
redirect_uri | Specifies the callback location where the authorization was sent. This value must match the redirect_uri used to generate the original authorization_code. | String | Yes |
code | Client identification code received in /authorize call response. | String | Yes |
Request headers
| Parameter | Description | Data type | Sample value | Mandatory? |
|---|---|---|---|---|
accept | Must be "application/json" | String | application/json | Yes |
authorization | Encodes the client ID and secret with Base64. Use the encoded information in the HTTP authorization header. | String | Basic<Base64 encoded client ID and secret> | Yes |
Content-Type | Must be "application/x-www-form-urlencoded" | String | application/x-www-form-urlencoded | Yes |
Response properties
| Field | Description | Data type |
|---|---|---|
access_token | An access token | String |
token_type | The audience of the token | String |
expires_in | The expiration time of the access token in seconds | Integer |
scope | The scopes contained in the access token | String |
Sample token CURL
curl --location 'https://example.com/token’ \
--header 'Content-Type: application/x-www-form-urlencoded' \
--header 'Authorization: Basic {encoded ClientID:clientSecret}' \
--data-urlencode 'grant_type=authorization_code' \
--data-urlencode 'redirect_uri=https://{ExpediaDomain}/sso/auth’ \
--data-urlencode 'code={Authorization code after login as part of callback to Expedia /sso/auth endpoint}'Sample token response
{
"access_token": "eyJhbGciOi.JSUzI1NiIsImtpZCI6Ilk1MkFDVXd3QV9SUzI1NiIsInBp.LmF0bSI6ImlrY20ifQ",
"token_type": "Bearer",
"expires_in": 1799
}Userinfo endpoint
The GET /userinfo endpoint is a backend API call which returns claims about the authenticated user based on the provided access token.
Request Headers
| Field | Description | Data type | Sample value | Mandatory? |
|---|---|---|---|---|
ClientId | Identifies the client. Must match the value preregistered in your identity provider (IDP). Obtained during either manual client registration or via the Dynamic Client Registration API. | String | Yes | |
Authorization | HTTP header used to send credentials or tokens to authenticate a user | String | Bearer [access_token] | Yes |
Response
| Field | Description | Data type | Sample value | Mandatory? |
|---|---|---|---|---|
membershipId | Identifier which uniquely identifies the Customer's account | String | Yes | |
optIn | Boolean flag if customer Opts in for marketing email | Boolean | true/false | No |
languageId | Preferred language for the user | String | en, fr | No |
channelType | Different platforms through which a user interacts with an application | String | WEB, MOBILE, TABLET | No |
firstName | First name of the Customer | String | Yes | |
middleName | Middle name of the Customer | String | No | |
lastName | Last name of the Customer | String | No | |
email | Email address of the Customer | String | No | |
programAccount | Loyalty related information | programAccount | Please refer to Add loyalty -> programAccount section below for Object details | No |
Sample Userinfo CURL
curl --location 'https://example.com/userinfo' \
--header 'client_id: {clientId}' \
--header 'Authorization: Bearer {acess_token from token endpoint}'Sample Userinfo response
{
"membershipId": "12345678",
"languageID": "en",
"middleName": "MiddleName",
"lastName": "LastName",
"firstName": "FirstName",
"email": "test@expediagroup.com",
"programAccount": {
"programId": "Gold",
"loyaltyAccountBalance": {
"value": "10000",
"currency": "Points"
}
}
}Add loyalty
As part of your template site, you can include the ability for your customers to earn loyalty points on their travel purchases. If you choose, your template can also allow your customers to use their accumulated loyalty points to purchase travel.
The same setup requirements as the standard implementation apply, as do many of the values. Only those that are different are included here.
In addition to the standard user information, the loyalty program setup will include the following values.
programAccount
| Field | Description | Datatype | Mandatory? |
|---|---|---|---|
programId | Identifier for the loyalty program the customer is affiliated to or the tier name associated with the loyalty program | String | Yes |
loyaltyAccountNumber | The customer’s loyalty account number; should only be populated if a secondary identifier (other than the unique membershipId) is required for loyalty operations | String | No |
lastFourDigitsOfCreditCard | The last 4 digits of the credit card the customer used for the booking | Integer | No |
accountName | Program name (if different from tier name) | String | No |
loyaltyConversionRatio | Ratio of how payment converts to points earned (for example, $1 = 1 point) | Double | No |
loyaltyAccountBalance | Current balance of customer’s earned loyalty points | Amount (please refer to Amount section below for Object details) | No |
Amount
| Field | Description | Datatype | Mandatory? |
|---|---|---|---|
value | Loyalty balance; nested under loyaltyAccountBalance | Long | Yes |
currency | The earn currency used by the loyalty program, for example, CAD, USD, POINTS, MILES; nested under loyaltyAccountBalance | String | Yes |