SAML v2 の概要
SAML (Security Assertion Markup Language) は標準的な SSO フォーマットです。その XML ベースのフレームワークにより、電子署名された XML ドキュメントを介した情報交換によるシームレスな認証を可能にします。SAML v2 (別名 SAML 2.0) は、2005 年以来、Web ベースのクロスドメイン SSO を可能にする標準プロトコルとなっています。
認証フロー
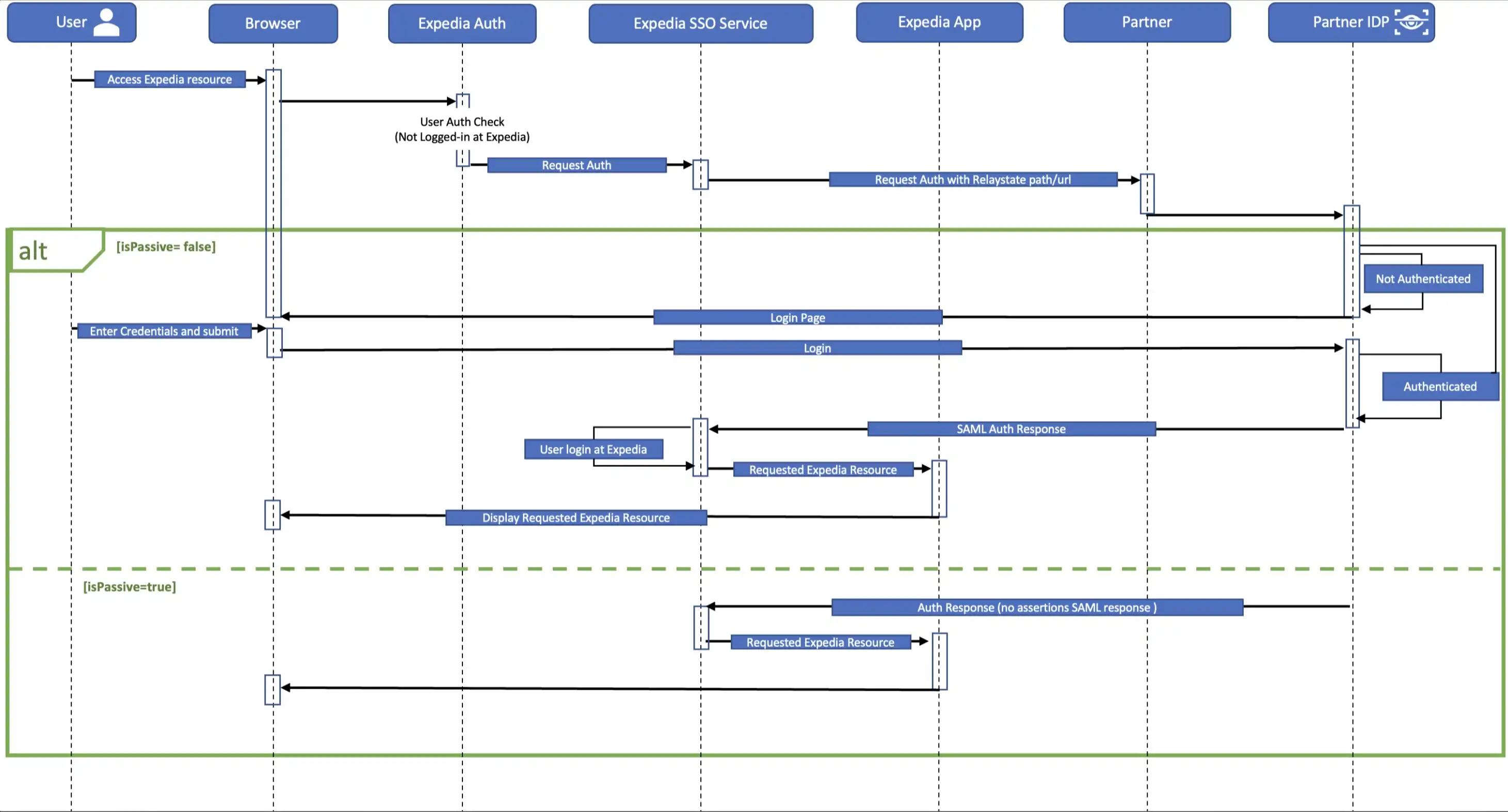
ベーシック SSO
選択した機能に関係なく、ベーシック SSO の設定要件は同じです。ロイヤルティまたはクレジット カードの実装を追加すると、追加情報が必要になります。
設定要件
テンプレートサイトへの SAML SSO アクセスを適切に設定するには以下が必要です。
- 公開鍵証明書 (署名検証用)
- 対象者
- 発行者
- エンドポイントの詳細
- 許可リストに追加する IP
- お客様フロー (isPassive) サポートの詳細
エクスペディアの標準的な SAML SSO 実装では、当社の公開鍵を使用して暗号化し、宛先エンドポイントを作成し、IP 許可リストを複製して妨害攻撃から保護します。
技術的要件 :
- サイトで使用されている SAML 2.0
- 秘密鍵は SAML レスポンス全体の署名に使用する必要があり、SAML ペイロードは Base64 でエンコードする必要がある
- エクスペディアの公開鍵はアサーションの暗号化に使用される
- SAML v2 標準に従って署名値を入力する
- SAML レスポンスに宛先と受信者を含める
- 適切な証明書を取得できるよう、SAML レスポンスに発行者を含める
ペイロードの詳細
顧客が ID プロバイダー (IdP) を介してログインすると、認証のために、生成されたレスポンス (ペイロードと呼ばれる) をメインサイトに送信します。認証に成功すると顧客にアクセス権が付与されます。エクスペディアが提供するペイロードには以下のフィールドがあります。これらすべてのフィールドが必須というわけではありませんが、ユーザーエクスペリエンス (たとえば、ウェルカムメッセージに顧客の名前を表示するため) や検証の一環としてこれらのフィールドの一部を使用します。
| フィールド | 説明 | 必須/必須ではない |
|---|---|---|
membershipId | 顧客アカウントの一意な識別子 | 必須 |
relayState | 認証完了後に顧客がリダイレクトされる URL | 必須 |
languageID | サイトで表示可能な言語 | 必須ではない |
channelType | サイトが最適化されているプラットフォーム (値 : WEB、MOBILE、TABLET) | 必須ではない |
firstName | 顧客の名 | 必須 |
middleName | 顧客のミドルネーム | 必須ではない |
lastName | 顧客の姓 | 必須ではない |
email | 顧客のメールアドレス | 必須ではない |
ロイヤルティの追加
テンプレートサイトの一部として、お客様が旅行の購入時にロイヤルティポイント を獲得できる機能を含めることができます。テンプレートでは、顧客が貯めたロイヤルティポイントを利用して旅行を購入できるようにすることもできます。
標準実装と同じ設定要件が適用されます。
ペイロードの詳細
標準実装に記載されている属性に加えて、ロイヤルティの獲得と利用の機能には以下のアカウント (ProgramAccount) 属性が必要です。
| フィールド | 説明 | 必須/必須ではない |
|---|---|---|
programId | ロイヤルティプログラムのステータス識別子 | 必須 |
programAccountNumber | 顧客が参加しているプログラムのアカウント番号 (別名 loyaltyAccountNumber) | 必須ではない |
lastFourDigitsOfCreditCard | 顧客が予約に使用したクレジットカードの下 4 桁 | 必須ではない |
accountName | プログラムアカウント名 | 必須ではない |
loyaltyConversionRatio | 支払いにおける獲得ポイント率 (例 : $1 = 1 ポイント) | 必須ではない |
loyaltyAccountBalance | 顧客が獲得したロイヤルティポイントの現在の残高 | 必須 |
支払いカードの制限
顧客が組織のクレジットカードを使用して予約するのを義務付けるようサイトを設定できます。すべてのテンプレートソリューションですべての主要なクレジットカードまたはデビットカード、および (米国では) PayPal を受け付けることができるため、これは必須ではありません。
クレジットカードの安全性と保管
組織のカスタムクレジット カードを使用して購入することを義務付けた場合でも、心配は無用です。クレジットカードは次のように扱われます。
- 顧客のエクスペディアプロフィールにリンクされた、トークン化された形式でカード情報が保存されます。暗号化されていない状態で保存されることは決してありません。
- 人間は暗号化されていないカードデータにアクセスできず、安全な IAM ログイン情報を使用しないと復号化できなくなっています。
- カードがチェックアウトページにプリロードされると、カード番号ではなくカードの説明のみが表示されます。
- 保存されたカードで予約を完了する場合、顧客はカードのセキュリティコードを入力する必要があります。
設定要件
標準実装の設定要件に加え、クレジットカードが追加されるとエクスペディアでセキュリティをさらに強化する必要があります。そのためには以下が必要です。
- AuthnRequest パラメーターに使用するエンドポイント
- 署名検証用の公開鍵
エクスペディアでは自社の秘密鍵を使用して AuthnRequest ペイロードに署名し、公開鍵を共有して貴社側で署名検証を実行してもらいます。
ペイロードの詳細
顧客がサイトにログインすると、標準実装で説明されている属性とともに、署名され暗号化されたアサーションを含むエンコードされた SAML レスポンスペイロードが、セキュアなエクスペディア SSO エンドポイントに送信されます。
ペイロードには次のクレジット カードの詳細も含まれます。
| フィールド | 説明 | 必須/必須ではない |
|---|---|---|
cardNumber | 請求対象のクレジットカードの番号 | 必須 |
cardType | 使用されるカードの種類 (例 : Visa、MasterCard、American Express) | 必須 |
expirationDate | 使用されるクレジットカードの有効期限 | 必須 |
addressCategoryCode | 使用されたカードに関連付けられているクレジットカード登録住所の種類 (例:自宅または会社) | 必須 |
firstAddressLine | クレジットカード登録住所の 1 行目 | 必須 |
secondAddressLine | クレジットカード登録住所の 2 行目 | 必須ではない |
thirdAddressLine | クレジットカード登録住所の 3 行目 | 必須ではない |
cityName | クレジットカード登録住所の市町村 | 必須 |
provinceName | クレジットカード登録住所の都道府県 | 必須 |
postalCode | クレジットカード登録住所の郵便番号 | 必須 |
countryCode | クレジットカード登録住所の国コード | 必須 |
AuthnRequest
認証されていないユーザーがテンプレートサイトにアクセスすると、エクスペディアは AuthnRequest と RelayState の両方のパラメーターをエンドポイントに送信します。これによりユーザーにログインを要求し、SSO プロセスを開始します。
AuthnRequest 要素には以下が含まれています。
| フィールド | 説明 | 必須/必須ではない |
|---|---|---|
AssertionConsumerServiceURL | ユーザーがログインした後のエクスペディアテンプレートサイトへの URL | 必須 |
Destination | AuthnRequest をポストするエンドポイントの URL | 必須 |
Issuer | データの出所 (値 : Expedia-Test または Expedia-Prod) | 必須 |
Signature | メインサイトで検証される SSO 署名 | 必須 |
詳細についてはペイロードサンプルをご参照ください。